Unraveling the Secrets of Montana's Internet
20% of the internet in Montana has critical vulnerabilities. Webcams are showing people's homes, businesses, and libraries. Computers, water pumps and wells, databases, and Content Management Systems are exposed. There's a lot to unpack here.

Montana. Known for its ruggedness. For its small population and massive prairies. For its vast plains and rugged peaks. For elk, grizzly bear, and cutthroat trout.
But what about cyber security? Or more aptly for this study, how secure are we here? Adversis's team of researchers set out to answer this question.
You've heard the term Internet Service Provider (ISP). ISPs are the companies that provide your home and business with access to the internet. They are responsible for connecting you to the World Wide Web, allowing you to access websites, social media, and other online services.
But have you ever thought about what else your ISP may be hosting, and who can see it?
It's all connected
Disclaimer: All research and information presented in this document were obtained solely from publicly available sources, and no actions were performed on any systems or networks to gather this data. The use of this information is intended for educational purposes and to raise awareness about cybersecurity best practices.
Adversis researchers gathered all of the technology companies in northwest Montana region and started asking the American Registry for Internet Numbers (ARIN) database certain questions. ARIN keeps track of all of the IP addresses registered to a company - this is public data.
Think of an IP address as a PO Box. There are only so many PO Boxes, and you can lease one from your local Post Office. If you no longer need it, another customer can lease that very same PO Box. For example, Montana Sky; a local ISP, leases a range of IP addresses, which they sublease to their customers.
As IP registration data and services are in a constant state of change, Adversis took a point in time snapshot of these northwest Montana IP addresses and began to gather publicly available data about what services were accessible at those IP addresses.
You're reading this website on port 443, which is a providing a web hosting service.
Imagine a port as a storefront in a shopping center. Passersby can see the shop, and sometimes they can enter and browse the store, other times, other times the shop is locked and a key is required for access, other times the shop is closed. In this case, the shop is open, no key is required, and you can browse the website.

Many businesses have software running that provides external access to their networks (commonly found on port 3389), or databases that manage their business (sometimes found on port 3306). Occasionally this is necessary and expected, but most often access to those services should be restricted to the business network or certain computers, not the entire internet.
The most common ports are numbered 80 and 443, which is where you find most websites. There are over 65,000 of these ports but most services are found on a select few ports.
What we found
Every cyber security framework has one thing in common. They all specify in one way or another that various administration and management ports and services shouldn't be accessible on the internet.
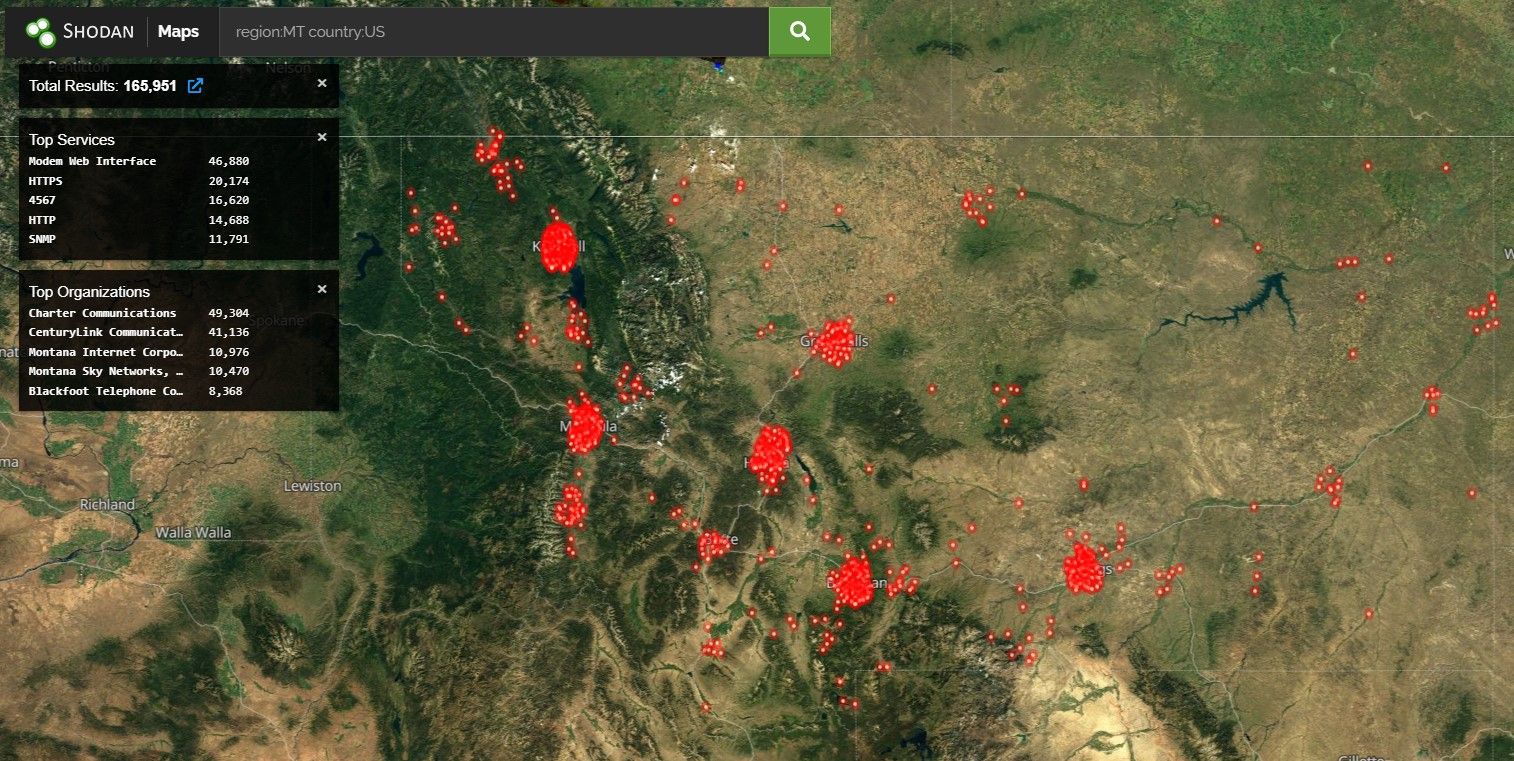
Adversis looked at 12 ISPs and analyzed 165,000 Montana IP addresses.
- Montana Sky Networks, Inc.
- 3 Rivers Telephone Cooperative, Inc.
- Montana Opticom, LLC
- Blackfoot Telephone Cooperative, Inc.
- Vision Net, Inc.
- Skylink Digital
- Arrow Group Inc.
- Bullitt Communications
- IP Routing LLC
- Montana Internet Corporation
- Mid-Rivers Telephone Cooperative
Of these IP addresses, over 50,000 have some form of vulnerable service meaning over 30% of devices are running out of date software.
And most concerning - over 10,000, or nearly 20% of these systems have a vulnerability that would allow a hacker to remotely crash the system or gain access to it by exploiting the code.
That's not to mention several hundred devices providing remote desktop access to systems and dozens of devices, servers, routers, Synologys, streaming services, PBX interfaces, network and WiFi management interfaces accessible with default credentials and outdated software.

Many of these services allow anyone on the internet to access services hosted by your business and home computers and networks. In the case of most websites, this is expected. But outside of that scenario, your risk begins to increase.
Dozens of screenshots highlight the prevalence of remote desktop allowing any internet user to access network systems, view usernames, and guess passwords.
With remote desktop exposed, you're only as strong as the password in use. And if you forgot one Windows update, an attacker may be able to bypass your password altogether.
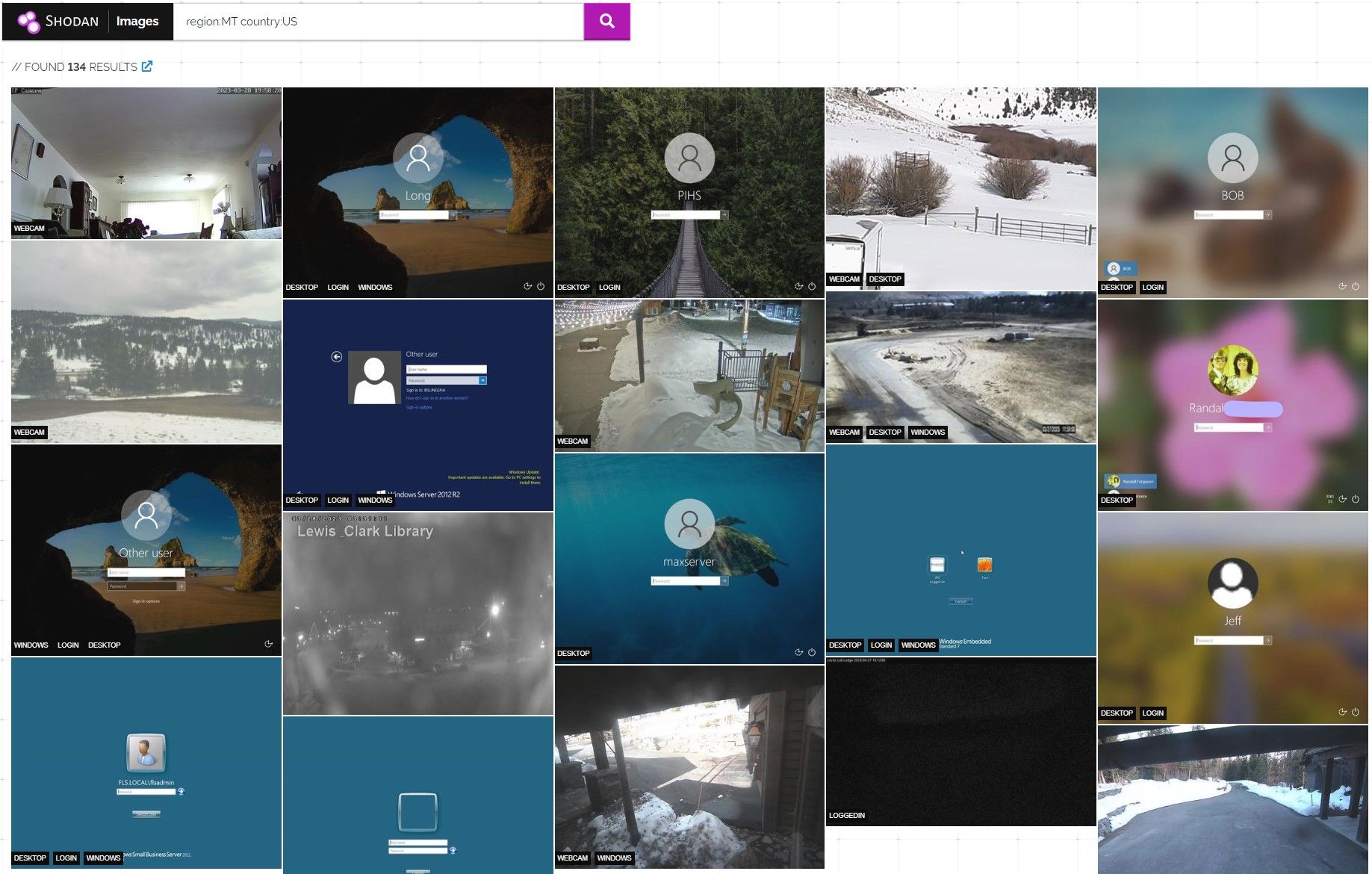
In one case researchers also found completely open databases and content management systems for local businesses which we have since reported to the affected business. In other cases, accounting firms have exposed their databases to the internet. And unfortunately in others, unprotected databases had already been compromised, with their contents ransomed.
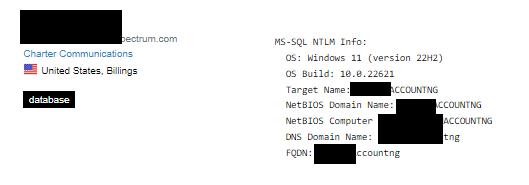
A SCADA system, or Supervisory Control and Data Acquisition system, is a computer system used to monitor and control industrial processes, such as power generation, water treatment, or manufacturing. It allows operators to keep track of real-time data and remotely control equipment, ensuring that everything runs efficiently and safely in large-scale operations. Think of it as the central nervous system of an industrial facility, helping to manage and oversee all the various components at work.
There's no way anyone would put SCADA systems on the internet right? Think again, in one case, an Adversis researcher found a SCADA system for a water treatment plant just 15 miles away from his home.
Several dozen SCADA systems were discovered requiring no authentication controls to view and potentially modify sensitive utilities. The vendor providing these water system SCADA control dashboards does not secure systems by default and leaves password settings up to their customers. This can potentially impact water supply and waste treatment which could directly impact local citizens.
In addition, Adversis determined over 700 organizations have their business names assigned dedicated IP space. You can check to see if your company is listed at this link. Ask your IT provider or ISP if your organization should have this configuration. And ISPs weren't immune to these risky exposed services - there are multiple cases of ISP management portals online.

Things are slowly getting better
Fortunately, it appears that the number of exposed IPs is slowly decreasing. After seeing a big increase in 2020 likely due to an increase in remote work from COVID-19.
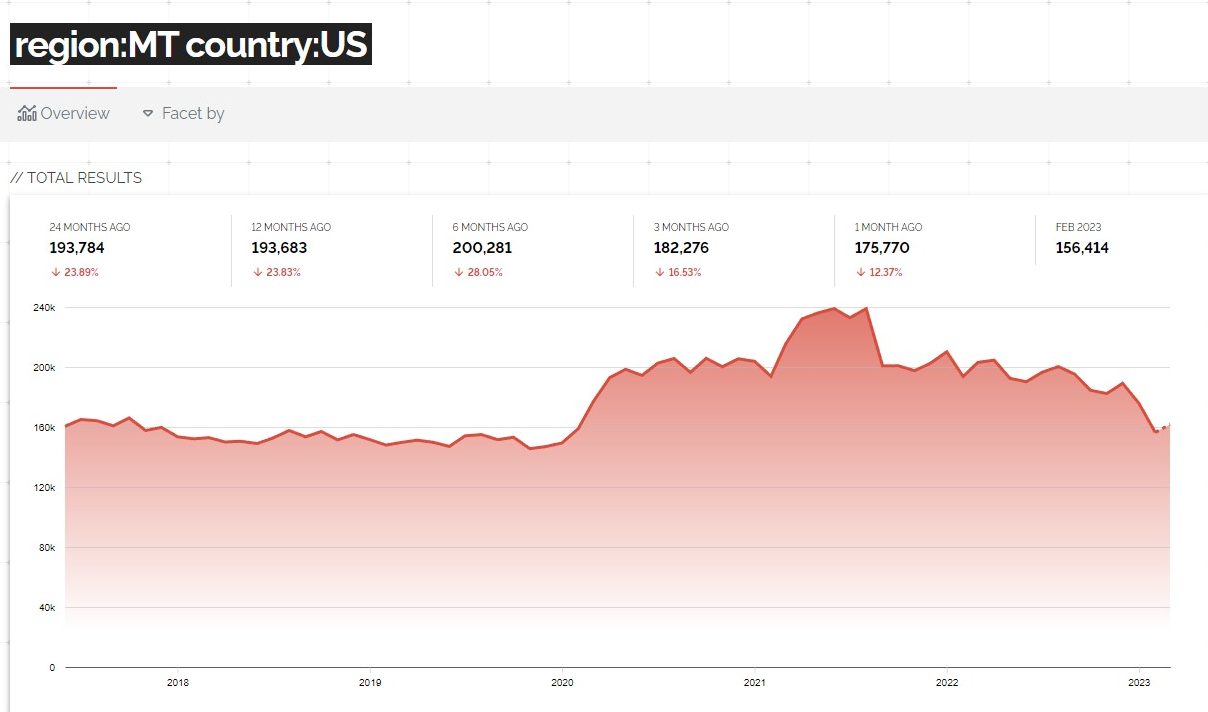
And it looks like vulnerabilities (noted as CVEs) have been slowly trending down over the past few years, though there are still far too many vulnerable systems accessible to the internet.
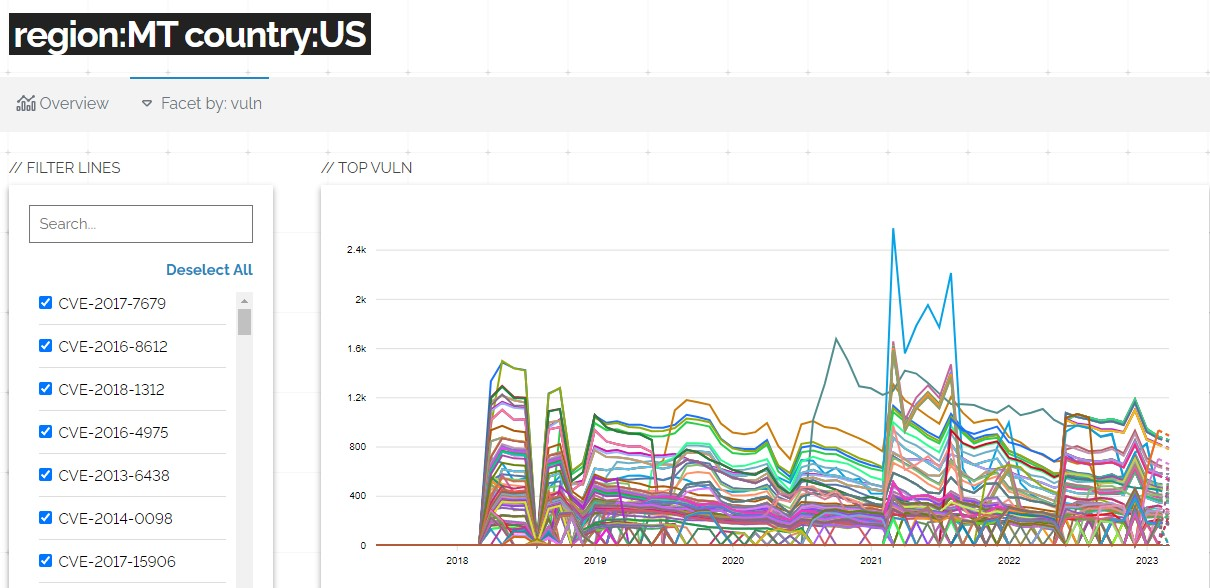
Hopefully these downward trends continue as customers inquire and require their service providers to securely configure and patch their networks and connected systems.
The Internet Search Engine
You can review this data as well. Shodan is a search engine that allows users to find specific types of computers and devices connected to the internet. It's Google for the Internet.
Shodan scans the internet looking for publicly accessible devices and servers. It then stores information about these devices in its database, making it easy for anyone to search for them.
How to check your exposure
So, how can you check if you are exposed on the internet search engine Shodan? It's easy, and there's no risk to check - remember, this is all public data, the same way that Google indexes documents it finds on the internet.
Adversis has created a simple way to check this. Go to WhatsExposed and click "Check My Exposure". Ideally you will see no results found.
If you do see results, your organization may be hosting services that are publicly accessible such as a website. This can be entirely normal and hopefully your administrators are aware of this. If you have remote access services accessible, consider restricting access to known IP addresses, and use MFA to log in. If you're not expecting exposed services, talk to your network administrators and they should be able to resolve it.
Trust, But Verify
Let's be clear: this isn't necessarily the fault of any one service provider.
It's most commonly a lack of communication and understanding. Service providers assume the customers are responsible for hardening systems and locking things down, and the customer often assumes the service provider is responsible. In the case of an IT team, they likely assume that the devices themselves are secure and don't always understand the intricacies or nuances of cyber security.
But we can't blame them. This is largely an education issue, and with some due diligence, you can keep yourself safe.
Hold your ISP and managed service providers accountable to provide secure services for you and your clients. Don't be afraid to ask questions, and be proactive about protecting your online privacy.
Cyber Security is a unique field of expertise and Adversis can help provide assurance. As we've seen, things are slowly improving as more people like you know to ask your vendors and service providers how they're keeping your business and systems safe from attackers. Let's hold them to it.
Get in touch today!
Contact: [email protected]
Adversis: https://adversis.io
Adversis ACS: https://acs.adversis.io


