Your Documents, ShareFile'd
Adversis did some brief public research on Citrix ShareFile websites and found over 9,000 customer subdomains, over half of which have links accessible to anyone who can identify them. It’s possible your company is among them.

Using Citrix ShareFile for document collaboration?
Adversis did some brief public research on Citrix ShareFile websites and found over 9,000 customer subdomains, over half of which have links accessible to anyone who can identify them. It’s possible your company is among them.
Of those companies, nearly 400 had some 9,000 documents shared; over 1.2 terabytes of data. These share links expose over 600 sharing users' emails and full names, and many allow anonymous users to upload files.
Unlike our prior experience identifying extremely sensitive information in Box, the publicly exposed ShareFile documents were by and large benign or public government documents. Many were shared by small businesses, consulting firms, as well as some state and government agencies. The most prolific sharers came from the San Francisco Public Utilities Commission, World Health Organization, Children's Trust Fund Alliance, and unsurprisingly, Citrix.
If you’d like to make sure your ShareFile account is configured securely enough to prevent simple compromise, follow along. We’ll talk about feature security and some account security settings.
It's All About Brand
As ethical hackers, we occasionally try to trick people into logging into web pages that aren’t legitimate to steal your credentials or get you to download malicious documents or software.
If one of your vendors was Trusted Partner Inc, would you trust documents shared here or attempt to log in?
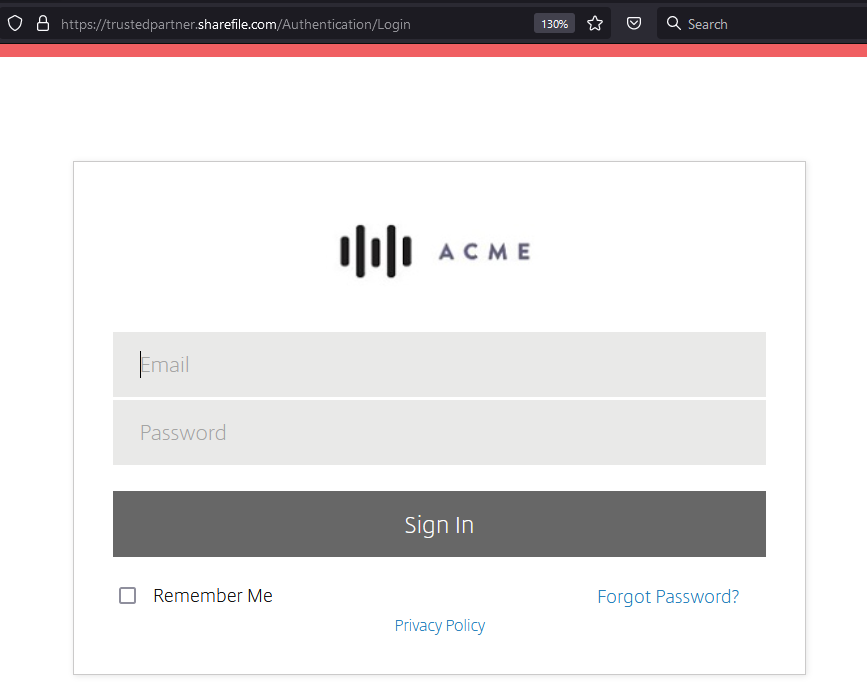
You too can create a page like this with a free trial account in about 3 minutes. Be careful about who and what you trust online!
Securely Sharing Files
Adversis has some experience finding interesting data exposures, specifically with Box, and we’ve learned you sometimes need to go out of your way to ensure your documents aren’t getting into the hands of unexpected people.
Fortunately, ShareFile doesn’t suffer from guessable file names since links look like this: https://example.sharefile.com/d-sacda9a142284cde662c33025feb8c548. Though they can still be exposed, they aren’t going to be guessed.
The default sharing options are actually not too bad and require sign-in to access files.
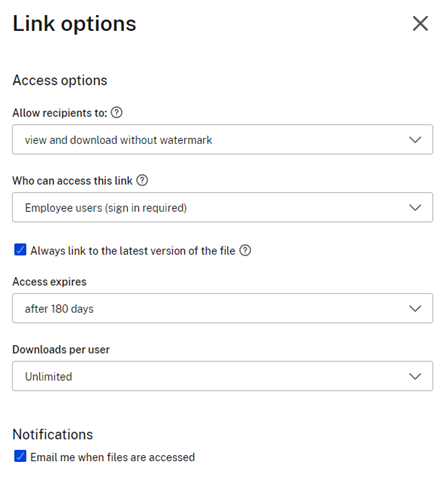
Requesting a Link leaves a little to be desired. Default is Anyone (anonymous) access that expires after 6 months. This is understandable if you need someone without an account to upload a file, but it would be best to expire access after a shorter time period. A quick Google search of these links returned over a dozen exposed documents.
Website File Uploads
Using this feature to allow people to upload documents from your website? I know it would be one of my first stops as a hacker to entice you to open a malicious Office document and compromise your computer. A quick open source search revealed over two dozen companies with this feature enabled.
Obviously, there are business needs for this feature but it's important to understand your risk exposure is increased. You'll probably want to be running secure workstations with the paid version of Microsoft's Defender for Business antivirus solution and the latest versions of all your business software at the least.
Drop those Files
Yet another feature I would be looking to abuse as an attacker. Even if your File Drop isn’t public, be cautious since these URLs can be exposed publicly through a variety of means. These links are random and can’t be guessed and look like this: https://example.sharefile.com/filedrop/dx3c7...5fab7e9.
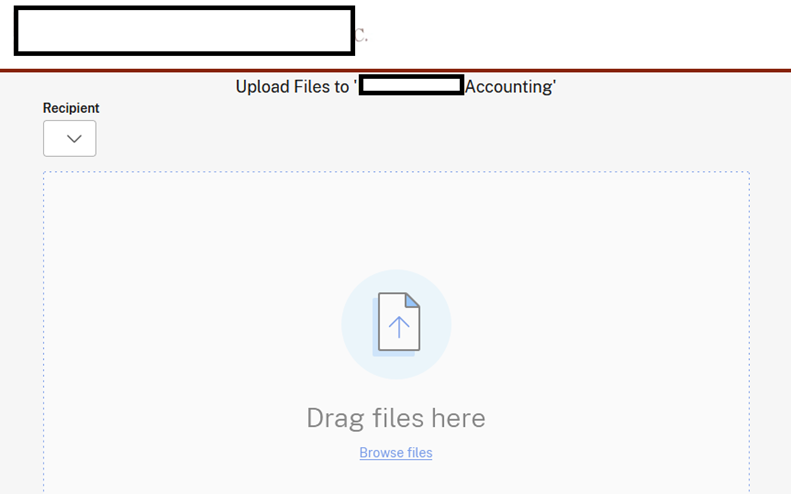
But it’s not a foolproof security measure. The below accounting firm has their public File Drop disabled but the random link was exposed and now anyone can browse to it and upload files to a specific user. Several dozen companies have these links exposed.
Question the Security of Security Questions
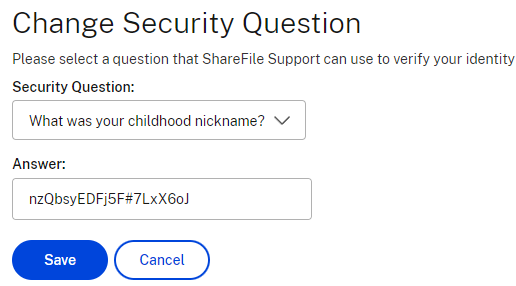
Don’t answer truthfully to security questions if you think anyone else might be able to guess or discover this information. Did you know this can be a random password? Use a password manager and store the answer there.
Require Decent Passwords
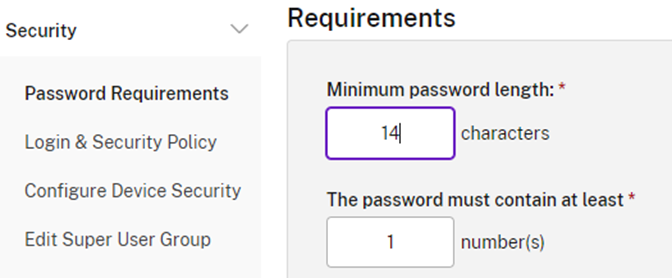
Worried about your documents being accessed by someone guessing weak passwords like Summer2022? Make sure your employees are using passwords they don’t use elsewhere and increase the required password length to at least 14 characters.
Enable Two-Step Verification
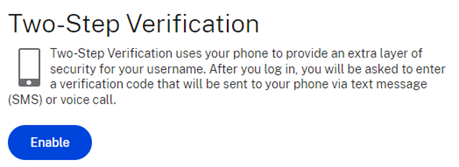
If the data you’re sharing is sensitive and you can’t afford to lose access to it or have it exposed, enable this feature. After you log in to your account but before you see your files, you'll have to enter a code sent to your mobile device. Conventional wisdom says this isn't foolproof but a criminal is much more likely to move on to the next victim before trying to bypass this feature.
Be Vigilant
Do these things, be vigilant about where you're logging in to and what files you open, and you'll be much further along than the next guy. As we say in grizzly country: you just need to run faster than the next guy.
Get in touch today!
Contact: [email protected]
Adversis: https://adversis.io
Adversis ACS: https://acs.adversis.io


